
Thunderbolt icon by jimmac
Thunderbolt 3 security levels
Thunderbolt is an I/O technology that can be used to connect external peripherals to a computer — similar to USB and FireWire. It works by bridging PCIe between the controllers on each end of the connection, which in turn means that devices connected via Thunderbolt are ultimately connected via PCIe. Therefore thunderbolt can achieve very high connection speeds, fast enough to even drive external graphics cards. The downside is that it also makes certain attacks possible (e.g. Thunderstrike, DMA attack).
To mitigate these security problems, the latest version — known as Thunderbolt 3 — supports different security levels:
none: No security. The behavior is identical to previous Thunderbolt versions.dponly: No PCIe tunnels are created at all, but DisplayPort tunnels are allowed and will work.user: Connected devices must be authorized by the user. Only then will the PCIe tunnels be activated.secure: Basically the same asusermode, but additionally a key will be written to the device the first time the device is connected. This key will then be used to verify the identity of the connected device.
The active security level can normally be selected prior boot via a BIOS option, but it is interesting to note that in the future the none option is likely to go away. This of course means connected thunderbolt devices wont work at all unless they are authorized by the user from with the running operating system.
Intel has added support for the different security levels to the kernel and starting with Linux 4.13. The interface to interact with the devices is via files in sysfs. Since July we have been working on the userspace bits to make Thunderbolt 3 support "just work" 😉. The UX design design was drafted by Jimmac. The solution that we came up with to implement it consists of two parts: a generic system daemon and for GNOME a (new) component in gnome-shell. The latter will use the daemon to automatically authorize new devices. This will happen if and only if the currently active user is an administrator and the session is not locked.
bolt 0.1 Accidentally Working
Today I released the first version 0.1 (aka "Accidentally Working") of bolt, a system daemon that manages Thunderbolt 3 devices. It provides a D-Bus API to list devices, enroll them (authorize and store them in the local database) and forget them again (remove previously enrolled devices). It also emits signals if new devices are connected (or removed). During enrollment devices can be set to be automatically authorized as soon as they are connected. A command line tool, called boltctl, can be used to control the daemon and perform all the above mentioned tasks (see the man page of boltctl(1) for details).
I hope that other desktop environments will also find that daemon useful and use it. As this is not a stable release yet, we still have room for API changes, so feedback is welcome.
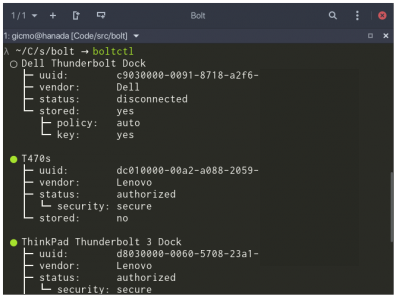
botlctl example output
New software needs testers, so everybody who has a computer with Thunderbolt 3 and feels courageous enough is welcome to give it a try. I created a copr with builds for Fedora 27 & rawhide and Jaroslav created a PKGBUILD file so Arch users can find it already in the AUR. As this is very fresh software it will contain bugs and those can be filed at the issue tracker of the github repo.
what's next: gnome-shell integration
I am locally running a Proof-of-Concept gnome-shell extension that implements the user session bits to complete the aforementioned : It uses bolt's D-Bus interface and listens for new Thunderbolt devices and then enrolls them, if the user is logged in. Since it can take a while until all the devices that are attached via thunderbolt are properly connected the daemon has a Probing property that is used to display a little icon as a way to inform the user that something is happening on the thunderbolt bus. All of this is already working quite well here on my test machine. In the next few days (weeks?) I will be working on integrating that code into gnome-shell. There are a few open UX questions that need to be addressed, but all in all things looking good.
thunderbolt activity indicator (aka cable snake)
Special thanks to Alberto Ruiz, Benjamin Berg, Hans de Goede, Harald Hoyer, Javier Martinez Canillas, Jaroslav Lichtblau, Jakub Steiner, Richard Hughes who all helped and supported this project during the last few months! ❤️
Pingback: Bolt Will Tackle Thunderbolt 3 Security on Linux – PingIze
Pingback: Links 16/12/2017: Mesa 17.2.7, Wine 3.0 RC2, Kdenlive 17.12.0, Mir 0.29 | Techrights
Awesome work!
I just enrolled my "ThinkPad Thunderbolt 3 Dock", and now I can use the connected USB devices even during pre-boot in 'secure' mode.
The only thing that slightly made me wonder was if I had to do anything to make the 'master' item in the list switch from "stored: no". It seems I don't though.
Pingback: RedHat Bolt aggiunge sicurezza al Thunderbolt – Italia Notizie
Pingback: 1+ year of Fedora and GNOME hardware enablement – Silicon Island
Pingback: Apports de Fedora à l'écosystème du Logiciel Libre - My Tiny Tools
Pingback: Charles-Antoine Couret: Apports de Fedora à l'écosystème du Logiciel Libre | Fedora Colombia
Pingback: Apports de Fedora à l'écosystème du Logiciel Libre | Linux Hub
Pingback: Episode 18 | This Week in Linux – TuxDigital
We are trying to get a G-Speed RAID using thunderbolt 3 to work on our Centos 7 server. boltctl shows up that the device is detected and authorized, and stored. The authflags is none. The policy is default and no key is used. In the bios we are using user authentication security level. Despite of this the G-Speed raid doesn't show up in /dev. mdadm also doesn't detect the raid.
Pingback: LWDW: Accidentally Working – LinuxGameCast
Pingback: Christian F.K. Schaller: Fedora Toolbox ready for testing! | Fedora Colombia
Pingback: Thunderclap and Linux by Christian Kellner